Privacy by Design
atPlatform overview
The atPlatform allows developers to create applications and services that, with no effort on their part, follow the Seven Privacy by Design Principals.
A developer using the atPlatform no longer needs to be an expert in the complexities of cryptography, network connectivity, and data synchronization. When using apps created on the platform, sharing data is as simple as saving data locally, deciding who the data should be shared with, and tagging those atSigns. With the atPlatform, there is no infrastructure or backend systems to set up and manage. Nor are there large, centralized data databases where everything can be surveilled by a company, system administrator, or even the developer themselves.
Therefore, instead of the way applications are structured today (Fig. 1) , where a person’s data is duplicated and owned by many different vendors, and the person must log in to access it:
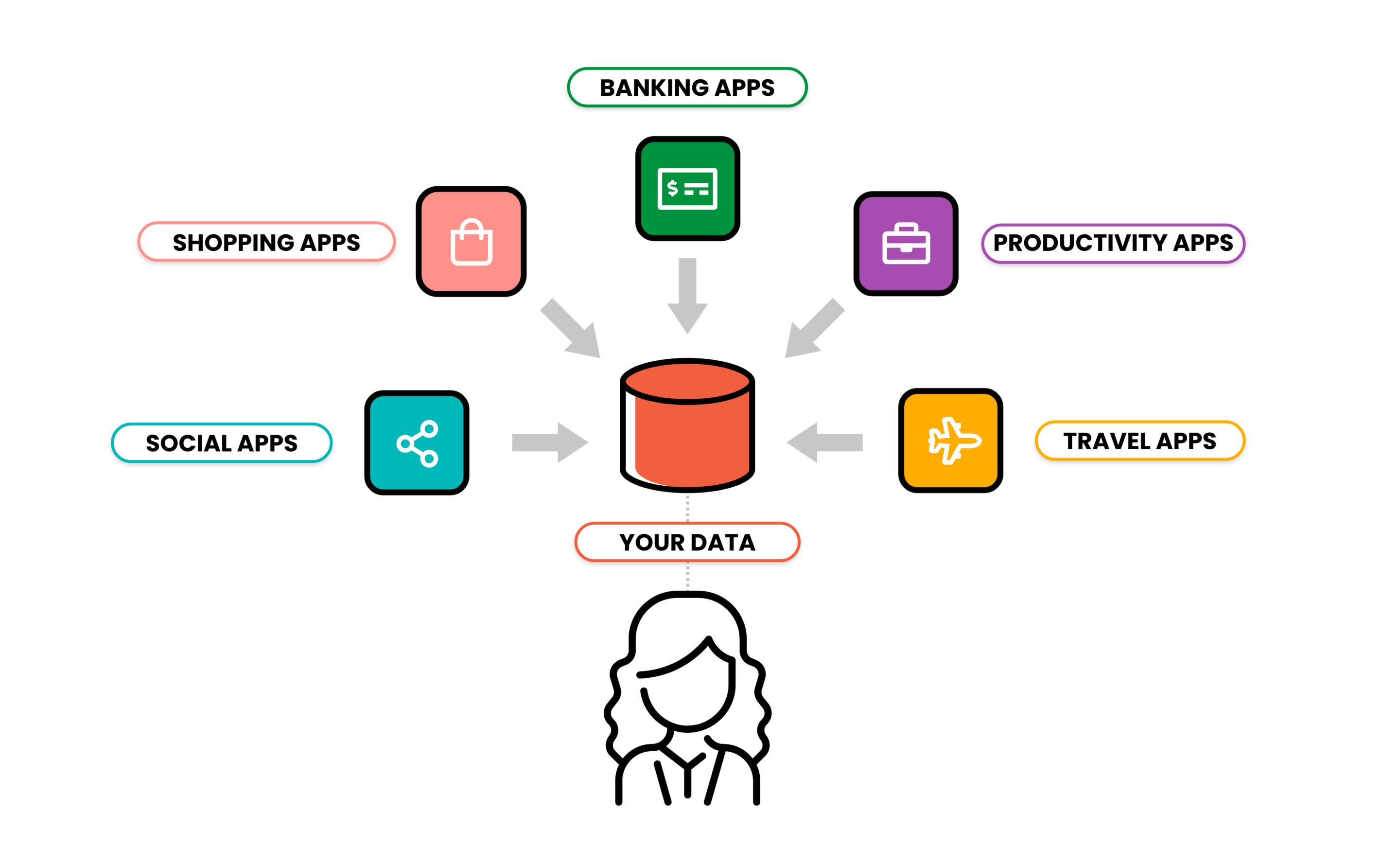
Fig.1 – How data is handled today
The atPlatform is a simpler, more streamlined architecture (Fig. 2), where the person’s data is all in one place so that they control it, and apps log into them:

Fig.2 – How data is handled by the atPlatform
To achieve all this, a new protocol had to be developed to provide addressability and allow self-generated cryptographic keys. With the open atProtocol, people, entities, or things each own a unique atSign address which can notify and allow other authenticated atSigns to collect data specifically encrypted for that atSign, and no other. The atProtocol specifies that every atSign has its own infrastructure, creating a completely distributed system. All data on that infrastructure that is not public is encrypted, and all public data has a cryptographic signature.
Principles of Privacy by Design
Privacy by Design was created by Dr. Ann Cavoukian and is now the law under the EU’s General Data Protection Regulation (GDPR). Privacy by Design encompasses IT systems, networks, and business processes.
Applications built on the atPlatform automatically incorporate these principles and provide the benefits of an even higher standard of privacy than what is mapped out in the privacy regulations of the GDPR and the California Consumer Privacy Act (CCPA).
The following are the Seven Principles of Privacy by Design, followed by how apps created on the atPlatform conform to those principles:
- Proactive not Reactive: Privacy by Design anticipates risks and prevents privacy-invasive events before they happen to build customer trust.
- The atPlatform has been built from the ground up to provide privacy, security, and control to the atSign owner. There is no centralization of consumer data. It is provably true that only the sender and the recipient can see the data in the clear.
- Privacy as the Default Setting: Personal data should be automatically protected – no action is needed by the user to protect their privacy, it is built into the system.
- The atPlatform is an open-source distributed system, where no data is centralized and all data is encrypted automatically, at rest and in transit. Developers need to have no cryptography experience to develop full end-to-end encrypted applications. Privacy is built in and not just a promise that could be broken in the future.
- Privacy Embedded into Design: Privacy is embedded into the design and architecture of IT systems, and becomes part of the product, service, or processes’ core functionality.
- The atPlatform and the underlying atProtocol have been designed from scratch to provide privacy and security for personal data. The architecture of the protocol forces the distribution of data so there is no centralized unprotected data.
- Positive Sum, Not Zero Sum: Privacy by Design avoids the false idea of trade-offs between privacy and security, showcasing that it is possible to have both.
- The atPlatform has no trade-off between privacy and security and, because of that, developers can provide new services and experiences.
- End-to End Security: Privacy by Design embeds security into the system from the start, which works to ensure a secure lifestyle management of information.
- The atPlatform creates a peer-to-peer, end-to-end encrypted, polymorphic system. Polymorphism is enabled because each party is mutually authenticated before any data is shared. As a result, the same query can yield a different answer depending upon the identity of the questioner. Controls such as Time To Live, Time To Birth, Time To Refresh, and Cascade Delete of remote data provide the basics of complete data control. But developers also can build and extend these data lifecycle constructs.
- Visibility and Transparency: Privacy by Design ensures operational execution aligns with policies. The end-user should know which data is collected, and for what purpose.
- People using the atPlatform have to explicitly add, and allow data access for, the atSigns with whom they want to share their data. Data access can also be rescinded at any point in time if they decide they no longer want to share their data.
- Respect for User Privacy: Privacy by Design develops trust by choosing user-centric measures: strong privacy defaults, appropriate notice, and empowering user-friendly options.
- The atPlatform provides an increasing number of user interface widgets for developers to use to quickly and easily build privacy compliant apps. Applications on the atPlatform do not own data, the data is owned by the atSign owner. This allows people to move to another application and take their data with them, without having to migrate their data to a new application.
Conclusion
The atPlatform allows developers to quickly and easily create Privacy by Design compliant apps and to concentrate on new experiences for their customers, without having to become experts in the complexities of implementing Privacy by Design.
Applications developed on the atPlatform inherit the strengths of the architecture of both the atPlatform and the atProtocol. The distributed nature of the platform also distributes, and limits, the risk of any intrusion to individual atSigns.
The atPlatform also allows for highly personalized services with strong authentication and without the need for providers to hold, and attempt to protect, personal information forever.
Atsign is allowing developers around the world to create end-to-end encrypted applications that provide new experiences on the Internet by incorporating privacy into the platform’s design from the outset.