ARTICLE
Shifting the Paradigm: Atsign’s Organic Security Approach

It’s challenging to fully explain the fundamental differences between Atsign technology and typical cybersecurity methods without delving into significant technical detail. This document provides a simplified overview of how Atsign’s approach to security diverges from traditional network access. In traditional networks, access is typically controlled through firewalls and authentication servers, creating a layered defense system. Atsign, however, takes a radically different approach, with a decentralized, zero trust architecture, encryption with keys that are cut at the edge, and a least privileged approach.
The Layered Defense Model
The current cybersecurity paradigm often resembles a fortified castle. A strong wall (the firewall) guards the entrance, but it has open gates (ports) that allow specific types of traffic. Attackers can exploit these open gates by disguising themselves as legitimate traffic. Once inside, they face checkpoints (authentication servers) that verify credentials (usually usernames and passwords). If they bypass these checkpoints, they gain access to the castle’s interior, where they can potentially move freely and seek valuable assets.
This layered approach has inherent vulnerabilities.
- Attackers can easily identify and exploit open gates, as evidenced by tools like Shodan.io and Censys that readily reveal publicly accessible services.
- Attackers can also easily guess or steal login credentials through brute-force attacks or phishing scams.
- Once inside the network, they can navigate the system (perform “lateral movement”) to access sensitive data.
To underline the issue, consider this: Despite a surge in spending on traditional cybersecurity methods, with Statista reporting a 78% increase from 2018 to 2023, the financial impact of cybercrime continues to skyrocket.
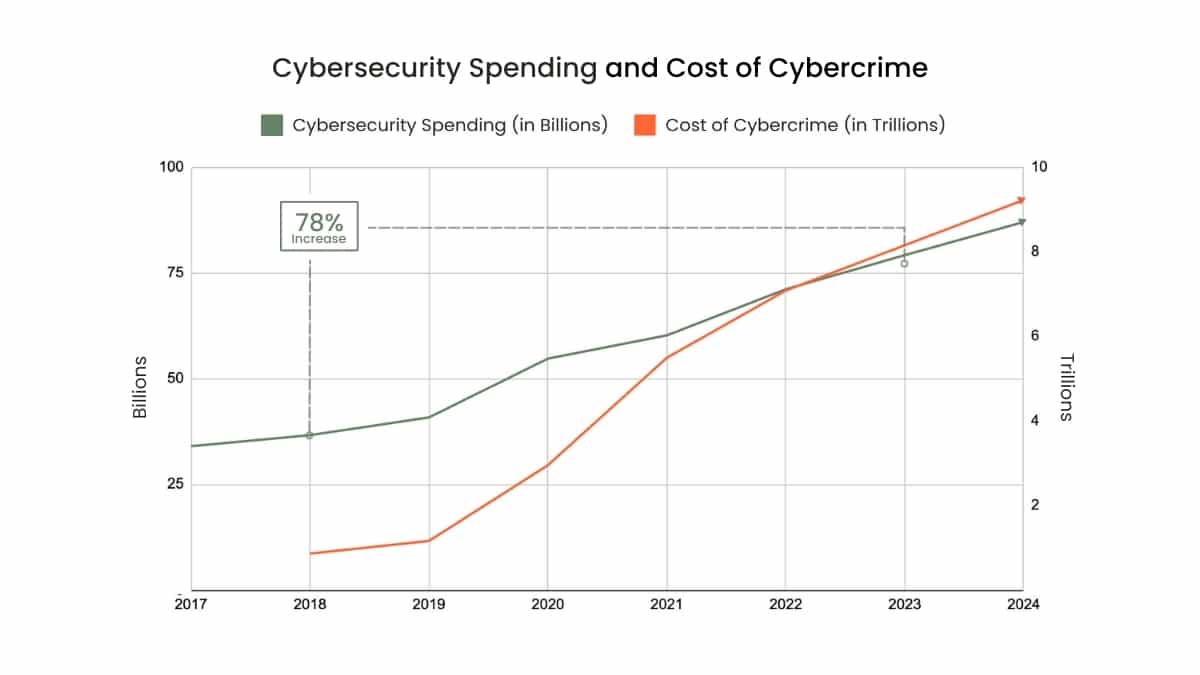
Source: Statista.com Worldwide Cybersecurity Spending and Cost of Cybercrime
Atsign’s Approach
Atsign takes a fundamentally different approach. Instead of a fortified castle, imagine walking up to an empty field . You can’t see the fortress (although it is there…somewhere), there are no open gates for attackers to exploit. Access is not granted by entering the domain, but rather by establishing secure, encrypted communication with a trusted intermediary outside—an atServer.
To interact with anything within this domain, you must first communicate with the atServer by using encrypted messages that only you and the atServer can read. The atServer verifies your identity using strong cryptographic methods.
You then give an encrypted message for the intended recipient within the domain to the atSever. Importantly, even the atServer cannot read the content of this message.
The atServer holds the message until the intended recipient retrieves it. The atServer cryptographically verifies the recipient’s identity before releasing the message.
The recipient then reviews the request and decides whether and how to respond. If they agree, they leave their secure domain and meet you at a pre-arranged location to fulfill the request. This prevents any unauthorized access to the recipient’s internal systems.
Learn More
Atsign offers a significant departure from traditional methods. By prioritizing secure communication, eliminating the need for open ports, and implementing strong cryptographic authentication, Atsign aims to enhance security and privacy in an increasingly interconnected world.
To learn more about Atsign’s technology and explore how it can improve your organization’s security posture, please visit the Atsign Documentation or schedule a consultation with our team.
SSH No Ports v4, Now with Windows Support and Expanded SDK
Revolutionary remote access tool, SSH No Ports, launches version v4 with Windows support and expanded SDK.
Networking 2.0: Privacy and Security
Networking 2.0 will revolutionize security and privacy on the Internet, especially for APIs.
Networking 2.0: Context
Networking 2.0 will revolutionize the way we communicate and interact with the world around us. Context is critical for better experiences.
Networking 2.0: Addressability
Networking 2.0 will revolutionize the way we communicate and interact with the world around us. Addressability is a key component.
Networking 2.0: An Introduction
Networking 2.0 will revolutionize the way we communicate and interact with the world around us. The next era of the Internet is here.




