Understanding Picosegmentation for Network Security
Why Your Network Security Needs an Upgrade
Traditional network security focuses on protecting the network perimeter. When a bad actor jumps those hurdles, they could gain access to your entire system. Microsegmentation was an attempt to prevent this lateral movement by dividing networks into smaller zones, limiting any breaches to the compromised zone and protecting the others.
Microsegmentation is effective, but it doesn’t scale. It is terribly impractical given the number of IoT devices, AI agents, and new services that need protection. It leads to thousands of these zones and a tangle of complex rules sorting out paths for authorized access.
How Picosegmentation Secures Everything in a Scaleable, Elegant Way
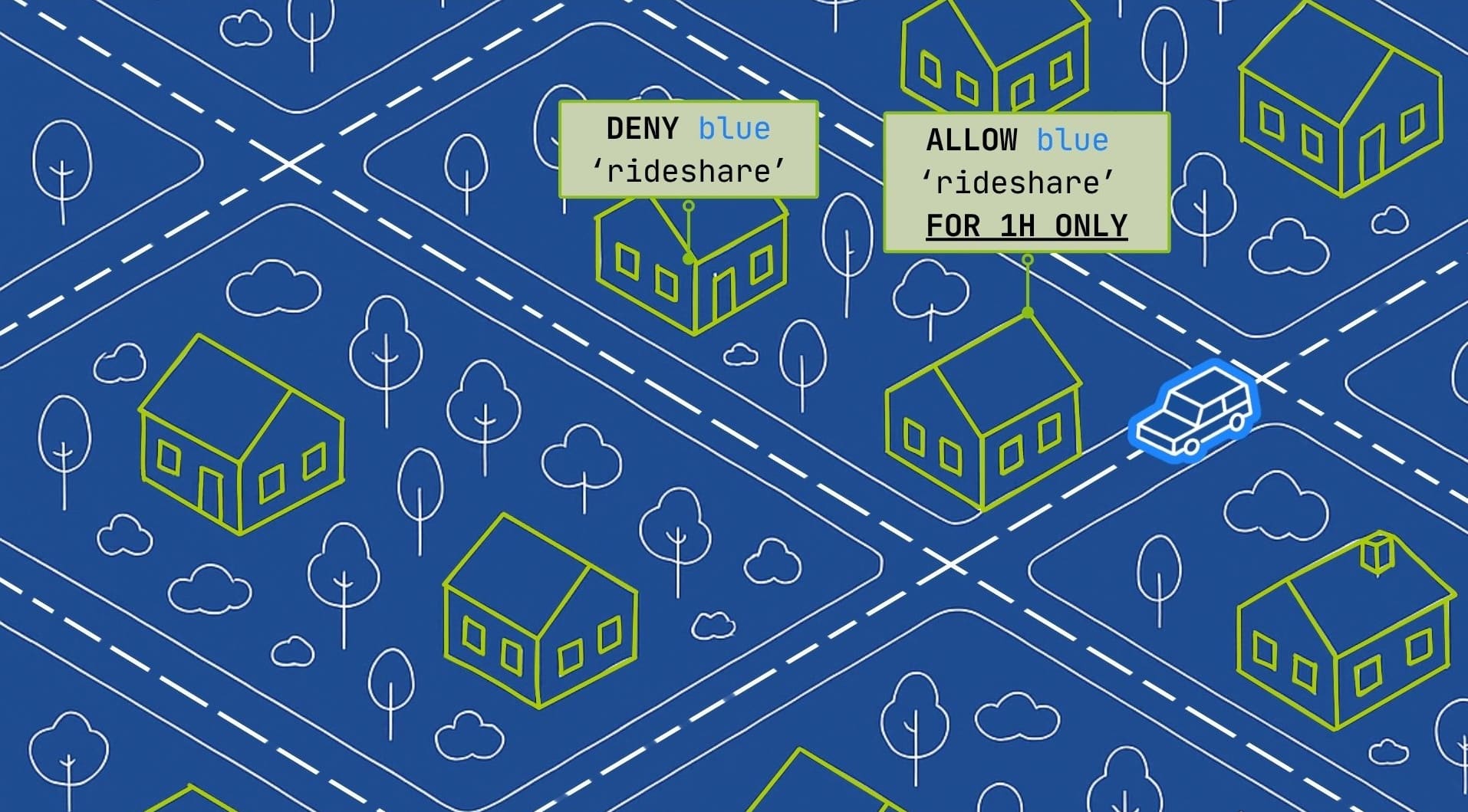
Instead of containing threats with a complex system of protected zones, picosegmentation secures all of the people, entities, and things in your network individually. This means every server, device, cloud instance, AI agent, and human is protected, even if the network is compromised.
This doesn’t mean you’ll need to spend a great deal of time setting up rules and permissions for every item. Instead, the atPlatform enables a flexible range of controls. These can be broad, coarse-grained controls, like giving a group of people access to a certain subnet. Or, they can be fine-grained, such as granting a specific doctor the ability to connect to a remote MRI machine for a limited time.
Here’s how it works:
Zero Trust
Nothing is trusted by default. Every interaction requires verification.
Authenticate Then Connect
Access is only granted after identity is confirmed, not before. This drastically reduces potential attack surfaces.
Individual Control
Security policies are applied directly to each element, rather than to broad network segments.
If an attacker compromises one device, their access is isolated to that single element. They cannot move to another part of your network.
Picosegmentation vs Existing Approaches
Here’s a straightforward comparison of network security approaches:
Picosegmentation offers the highest level of security available today, with significantly lower complexity and maintenance.
Implementing Picosegmentation Practically with the atPlatform
Unlike microsegmentation, which often requires a complete network overhaul, you can implement picosegmentation with the atPlatform incrementally.
Start with your most critical assets. For example, remote access for admins to key servers, or securing new IoT devices and AI agents as they come online. Over time, you can gradually extend atPlatform-powered picosegmentation across your entire network, strengthening your security layer by layer while also benefiting from other atPlatform advantages.
The atPlatform cryptographically verifies every interaction on your network. This ensures that only authenticated and authorized entities can connect. Its policy engine then lets you set and enforce individual-level security policies, making picosegmentaion possible, scalable, and attainable for your organization.
Contact us today to enhance your security!
Featured Resources
Where CEO Vision Meets CISO Approval: Launching AI Architect
AI Architect solves the enterprise AI bottleneck by combining visual architectural blueprints with a Zero Exposure foundation, allowing leaders to deploy secure, production-ready AI agents at 100x the speed of traditional coding.
The SDLC is Broken: Building Architectural Trust for Agentic AI
The SDLC is broken. As AI moves from chatbots to autonomous agents, here is how the architecture of trust must change.
The MCP Security Paradox: Why the “USB-C for AI” Is an Architectural Minefield
Model Context Protocol promises universal connectivity for AI, but its current architecture is scaling a broken trust model that leaves sensitive enterprise data vulnerable to exploitation.