ARTICLE
Zero Trust You Can Actually Trust

There are a lot of companies out there advertising their security and privacy offerings. While we believe they are well-meaning, at the end of the day, they can still see your data–even if they pinky promise not to look at it.
So, why should you trust Atsign? Why is Atsign different from these other companies? Simply put, we can never–EVER–see your data!
What We Are About
Atsign’s award-winning technology is built using Networking 2.0 principles. Here are some important facets of our tech:
Open Source
- Anyone can view the source code and scrutinize, verify our claims, and even help improve the code.
Distributed and Peer-to-Peer
- Our tech does not rely on transmitting data through a centralized server; all information exchange is peer-to-peer, directly to the recipient’s private server, with no third-party snooping possible.
Cryptographically Secure
- Uses the tried and true, industry-standard encryption technologies we all know and trust.
Zero Trust
- Devices cut their own cryptographic keys right on the edge. Only the owner of the device and the intended recipient can ever see the data exchanged between them.
Testing the Tech
Crucially, we believe in rigorously testing our technology, not only in-house, but also from external and reputable organizations. Read more about how our technology (specifically, SSH No Ports) stood up to pen testing.
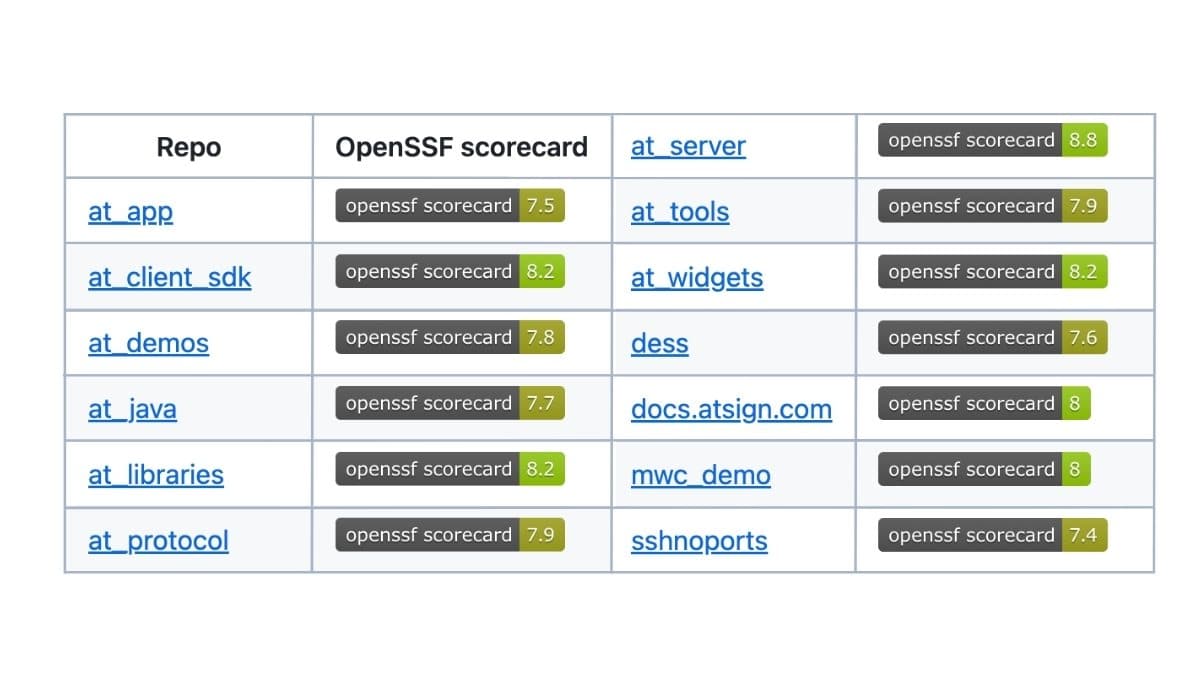
How secure is our code? We invite you to take a look. We have been using OpenSSF scorecards on all our key code repositories, and our scores are available for everyone to see. We take pride in our scores, and you will notice that our repositories rank among the best out there.
Here is a summary of our OpenSSF scores:
If you would like to learn more about OpenSSF, check out this blog post by Chris Swan who has been leading these efforts for us and also educating the community in the process through his various presentations, like this one from QCon in New York this past June.
Your Digital Doors Are Wide Open: An Urgent Warning
The FBI warns open network ports are critical security flaws. Learn why eliminating these “digital doors” is vital to protect your organization from cybercriminals and secure your future.
Understanding Picosegmentation for Network Security
Picosegmentation protects individual elements, simplifies management, and defends against lateral movement. It is a secure and easy to maintain alternative to microsegmentation.
Quick, Easy, & Secure GPU Arbitrage with Atsign’s atPlatform
Learn how atPlatform enables secure GPU arbitrage while cutting costs, minimizing downtime, and simplifying workload migration.
New Legislation Poised to Give People More Control Over Their Data
Utah has passed the Digital Choice Act, landmark legislation that could reshape how social media applications handle people’s data.
Shifting the Paradigm: Atsign’s Organic Security Approach
Atsign’s built-in security—encryption, zero trust architecture, and a least privilege approach—performs better than firewalls and authentication systems.