ARTICLE
The $200 Billion Paradox
Why Our Cybersecurity Industry Is Fundamentally Broken
The evidence is clear: the global cybersecurity industry is struggling with a fundamental structural problem.
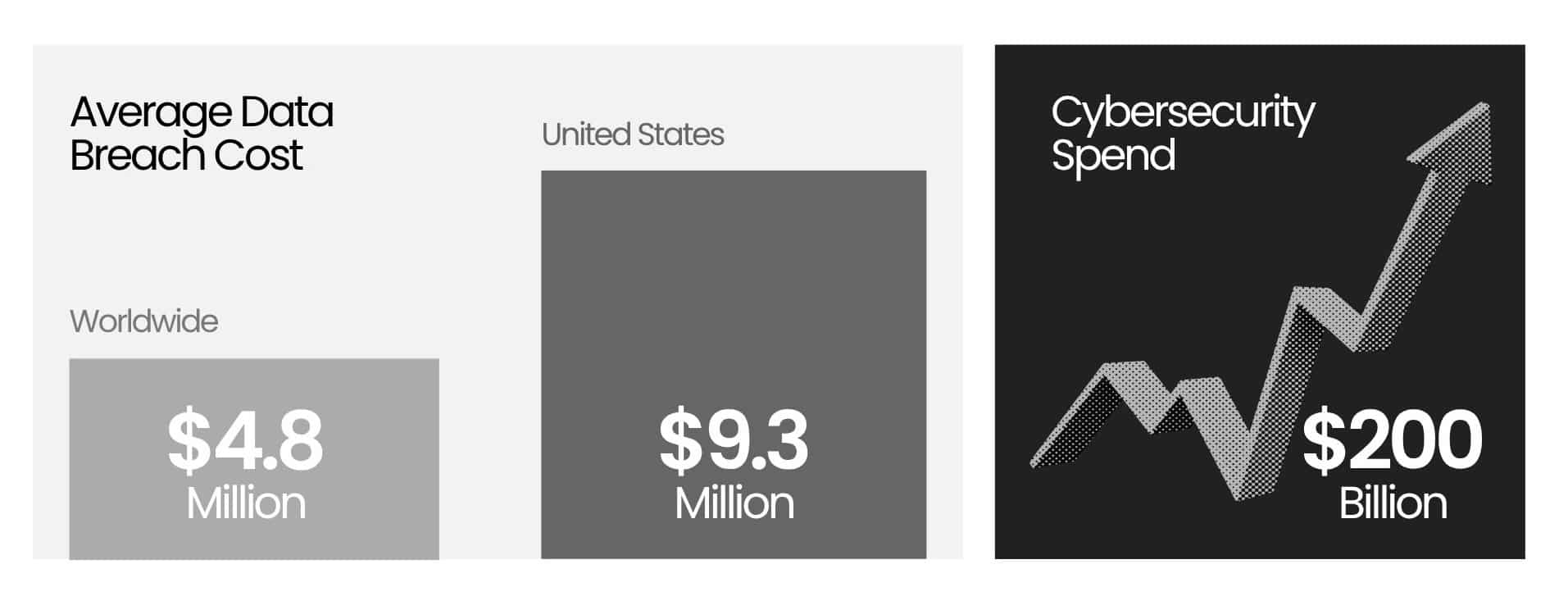
Cybersecurity spending is at an all-time high. It’s projected to exceed $200 billion annually1…yet the attacks keep getting worse. The average data breach now costs $4.88 million globally, and over $9.3 million in the U.S.2, with both figures continuing to rise. Why? Because the industry has become dependent upon a flawed economic model that rewards complexity and liability transfer over actual preventative security.
1. The Root Failure
The root problem is architectural: the current approach to network and system access is obsolete. It’s a model built before Zero Trust was even a concept.
This traditional approach fails in two critical ways: it exposes open entry points to the entire world, and it allows connection attempts before any authentication is even made. This gives malicious actors something to target and an avenue to exploit vulnerabilities.
To compensate, the industry has layered on complex defenses—firewalls, VPNs, proxies, and behavioral analytics. While these layers made attacks more difficult, they created administrative nightmares and still left countless holes. The industry’s ultimate response hasn’t been to rebuild; it’s been to pivot from Endpoint Protection (EPP) to Endpoint Detection and Response (EDR). This is a big concession. It’s an admission that hackers will get in, and all we can do is monitor them once they’re inside. This movement toward detection signals the industry’s acceptance that cybersecurity is currently a losing game.
This shift means:
- We’re reacting to zero-day attacks instead of preventing them.
- We’re spending millions on solutions that only promise to “tell you when there’s an issue,” not to eliminate the issue in the first place.
2. The Economics of “Covering Your Assets”
The deeper failure is simple: The focus is no longer security; it’s liability. The economics of the industry actually penalize true prevention.
There’s a belief that the architectural problem is unfixable, and regulatory pressure is immense. Therefore, many enterprise decision-makers default to purchasing liability transfer, like ZTNAs. They select the largest, most established vendors to establish “due diligence” and create a clear chain of accountability. This strategy ensures the organization can mitigate legal and reputational risk when a breach occurs, something the industry appears to accept as inevitable. This is done by pointing to their considerable vendor investment. However, this outsourcing never delivers a true zero trust solution (even though “zero trust” is in the solution’s name).
This mindset is fueled by learned helplessness. Since the problem seems too hard to solve, we’ve settled for the next best thing: paying someone else to take the blame.
This strategy drains resources into “compliance theater” rather than resilient architecture. We funnel cash toward proving we met a checkbox, even though the true cost is the massive expense of lost business, reputational damage, and customer churn, making up 43% of total incident costs3.
3. Centralization Is a Systemic Risk
The reliance on these major vendors as “liability sponges” introduces a massive, structural danger: systemic risk.
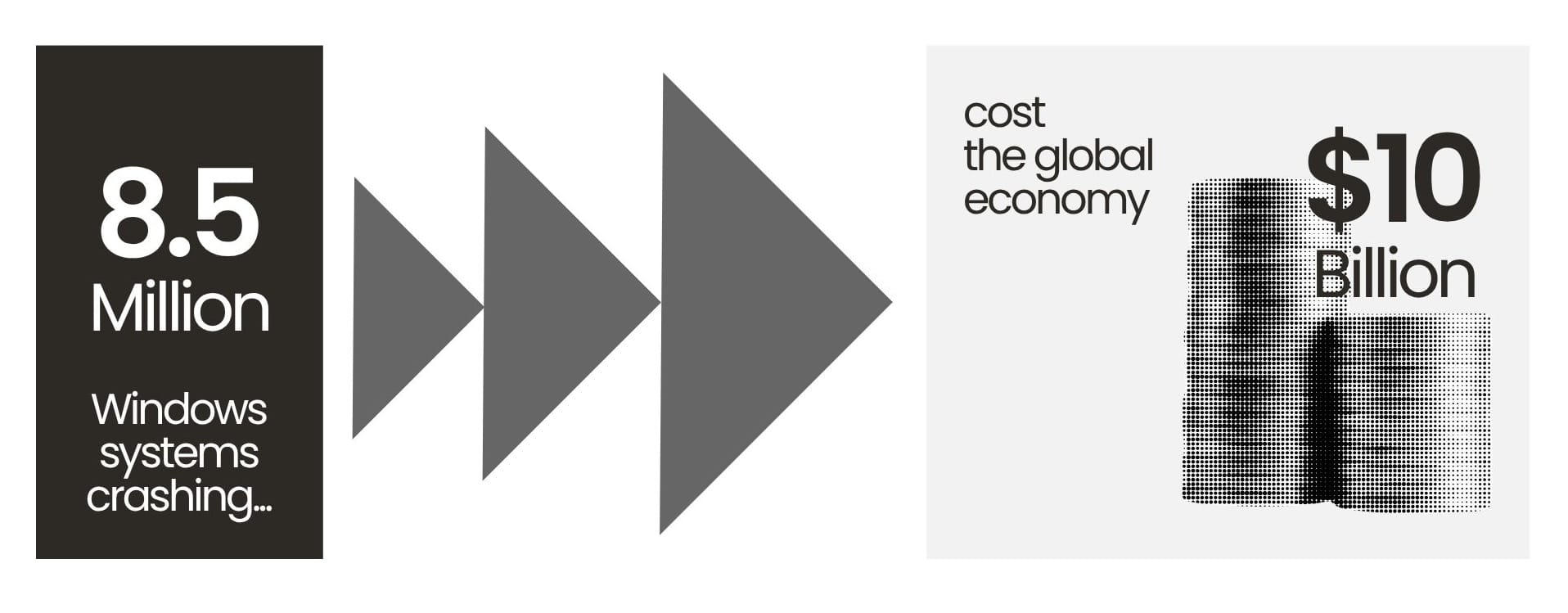
The 2024 CrowdStrike outage proved this point brutally. This wasn’t a hacker; it was an accidental vendor configuration error that crashed an estimated 8.5 million Windows systems worldwide and cost the global economy over $10 billion. This incident showed that when organizations rely on highly centralized security solutions, they create a catastrophic Single Point of Failure (SPOF). This strategy to “cover your assets” is actually putting a giant single kill-switch on the company’s entire operation.
The Way Out: Preemptive, Networkless Zero Trust
If we want to win, we have to stop playing the perimeter game. IT, network, and security teams deserve a smarter foundation. We must move to a true Zero Trust Architecture that is Identity-Centric and Networkless. This means we move from reactive security software inspecting anonymous inbound traffic to preemptive identity verification before any connection is ever made.
This architecture delivers a radically simpler and inherently more secure foundation:
- Instead of Open Ports – We get a Networkless model with zero inbound attack surface.
- Instead of Complex Equipment – We get outbound-only connectivity that doesn’t require VPNs or other overlay networks and greatly reduces the complexity of firewalls and other, or non-scalable “solutions.”
- Instead of Outsourcing Trust – The organization regains control of its encryption keys and trust, eliminating the need for a third-party broker.
- Instead of Closed Systems – You gain the open source transparency and auditability necessary for a security-first solution.
With this approach, true zero trust stops being a theory—it becomes beautifully real. This moves us from a reactive, detection-based model (where we wait for the attacker to enter and then try to spot them inside) to a proactive prevention model where the target is simply invisible.
The best news is that organizations can start this transition today. Protecting high-value assets is achievable before the end of the year, providing a peaceful holiday season and a better outlook for 2026.
2 Source: IBM: Cost of a Data Breach Report 2025
3 Source: IBM: Cost of a Data Breach Report 2025
4 Wikipedia

