Everything you need to know about end-to-end encryption (E2EE)
What is end-to-end encryption (E2EE)?
End-to-end encryption, also called E2EE, is a secure communication method where only the people sending and receiving a message or file can view its contents. This keeps the data from being seen by anybody else, including those who manage the service being used.
Your Title Goes Here
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.
How exactly does it work?
When you send a message/file, your data is encrypted before leaving your device. Anyone who accesses your encrypted data files will need the correct cryptographic keys to decrypt it.
For end-to-end encryption to work properly, both parties (the sender and recipient) must have two keys: a private key and a public key.
Anyone can access your public key, regardless of their identity. It can be used to encrypt files, but cannot be used to decrypt the same files.
You are the only one who can access your private key. You’ll need it to decrypt any files that have been encrypted using your public key.
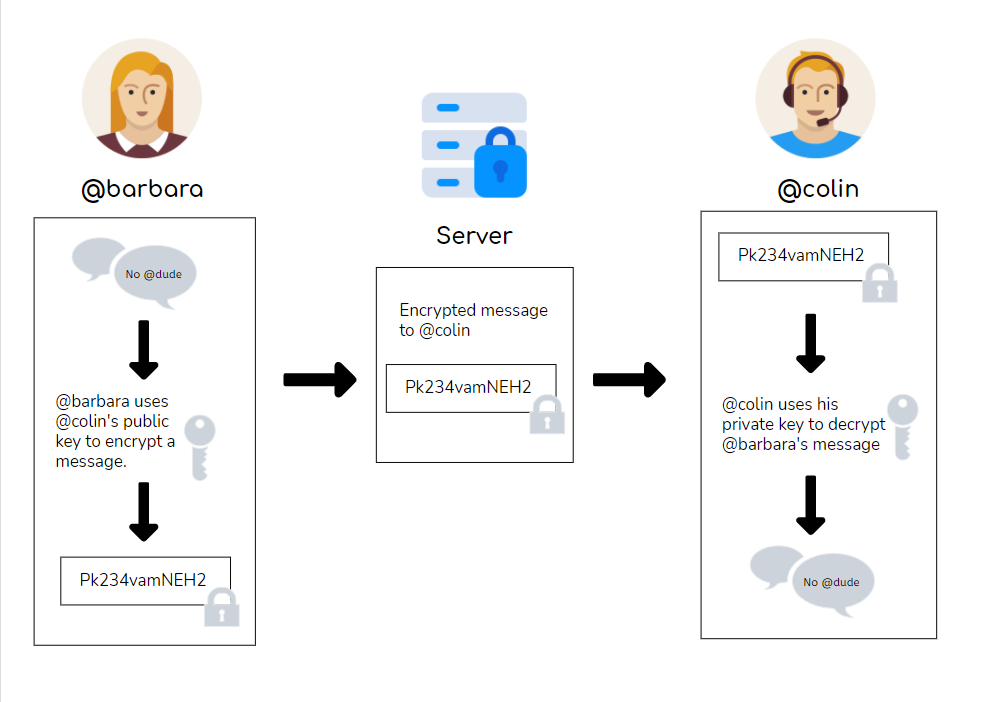
Let’s use @barbara and @colin as examples to further illustrate how public and private key pairs work.
Suppose @barbara sends @colin a message. Before the message leaves her device, she uses @colin’s public key to encrypt it.
The message travels through a server on the cloud before it reaches @colin’s device. However, anyone who sees this message cannot decrypt the message and read its contents, because they do not have access to @colin’s private key.
When the message reaches @colin’s device, @colin can use his private key to decrypt it and read @barbara’s message. The file has travelled safely from @barbara’s device to @colin’s device without any unwanted parties viewing it!
How to know if something is end-to-end encrypted
Unfortunately, there’s no easy way to verify that something is end-to-end encrypted unless the code is open source and freely available. And although open source code may prove that a certain software uses end-to-end encryption, that does not mean that your data is completely secure.
For example, let’s suppose that you’re using an app that claims to be end-to-end encrypted. You check the open source code and confirm that the app does indeed use end-to-end encryption. That means that your data is totally safe — right?
To answer that question properly, you need to ask yourself: Where are your keys, and who has access to them? There are two main possibilities:
❌ Not So Good Answer: Your keys have been saved somewhere not on your device.
If you’re not given the option to save your keys somewhere, then it means that your keys have probably been saved somewhere else. But if anyone else has access to your keys, then your information is no longer 100% confidential.
Another clue that your keys have been saved somewhere else is if you do not need to upload your keys to log into the service. Sometimes, you can log into your account just using a username/password, PIN, or phone number. Although this is convenient, it also means that your keys must be saved somewhere in a database that is linked to your login details.
If anyone can access your keys through a username or phone number, what was the point of all that cryptography? A hacker (or anyone who knows your information) could just hack into that company’s database and use your login information to access your keys.
- Your service provider stores your keys in a secure location (not on your device), linking them to a username/password, PIN, or phone number.
- Your service provider gives your keys to anyone who provides the correct username/ password, PIN, or phone number — even if they are not you.
- This person (who is not you) can now read all of your encrypted files and messages.
✔️ Good Answer: Your keys are saved on your device and nowhere else.
Owning your own keys means that you are in full control. A company that stores your keys for you may very well have good intentions, but if their systems are compromised, a hacker could access your keys and therefore all your data.
You’re also less likely to be hacked. What’s more appealing to a hacker: a large company database with thousands of keys, or a device that only holds one person’s data? If you own your own keys, then you’re less likely to be a target for hackers.
It’s important to note that if you lose your keys, recovering them may be difficult. There are certain workarounds — if you are already logged into an app or service, you may be able to redownload the keys on your device — but be sure you save them somewhere safe!
Your Title Goes Here
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.
What can I do if my keys have been saved somewhere else?
Unfortunately, not all end-to-end encrypted services will give you exclusive ownership of your keys. That does not mean that you cannot still benefit from the extra layer of protection that these services provide. Just make sure that you’re aware of the potential risks before sharing information that you might not want anyone else to know.
What end-to-end encryption protects (and does not protect)
End-to-end encryption ensures that the contents of your messages and files are private. It double-checks the identity of the person receiving your messages or files before allowing them to view what’s inside. No one else, not even the company running the service, can access your communications.
However, end-to-end encryption does not necessarily protect your behavioral metadata. Outsiders may not be able to read the messages, but they can still trace your behavior by paying attention to who you’re talking to and how often you’re talking to them.
Key Terms
Encryption
the process of converting information into secret code that hides the information’s true meaning
Decryption
the process of restoring encrypted information to its original format
Cryptographic Keys
strings of data used for different cryptographic functions, including encryption and decryption
Public Key
a cryptographic key that can be obtained and used by anyone to encrypt messages intended for a particular recipient
Private Key
a cryptographic key known only to the recipient, used to decrypt messages encrypted by that recipient’s public key
Behavioral Metadata
data that tracks online behavior, such as who one interacts with or the frequency of one’s interactions with specific people