ARTICLE
Introducing Picosegmentation
Microsegmentation was a good start—now let’s make it more secure and easier to maintain

By Barbara Tallent
The Introduction of Microsegmentation
Microsegmentation was first introduced around 2014 by VMware. The idea was simple: break up the network into smaller pieces so that if someone gets in, they don’t get everything. Instead of the attacker gaining access to your whole environment, they’re limited to one slice. It was a good idea at the time.
The idea started with the (Swiss) banks and the notion of a “network zoning concept.” The arrival of Software Defined Networking (SDN) presented a much easier way to create and manage all those zones.
Microsegmentation meant defining security around applications, environments, tiers, or groups of people You’d build smaller zones inside your network, often with software firewalls, and then write rules for what could talk to what. It was a step up from broader network segmentation, which mainly divided traffic by subnets or VLANS.
The Limitations of Microsegmentation
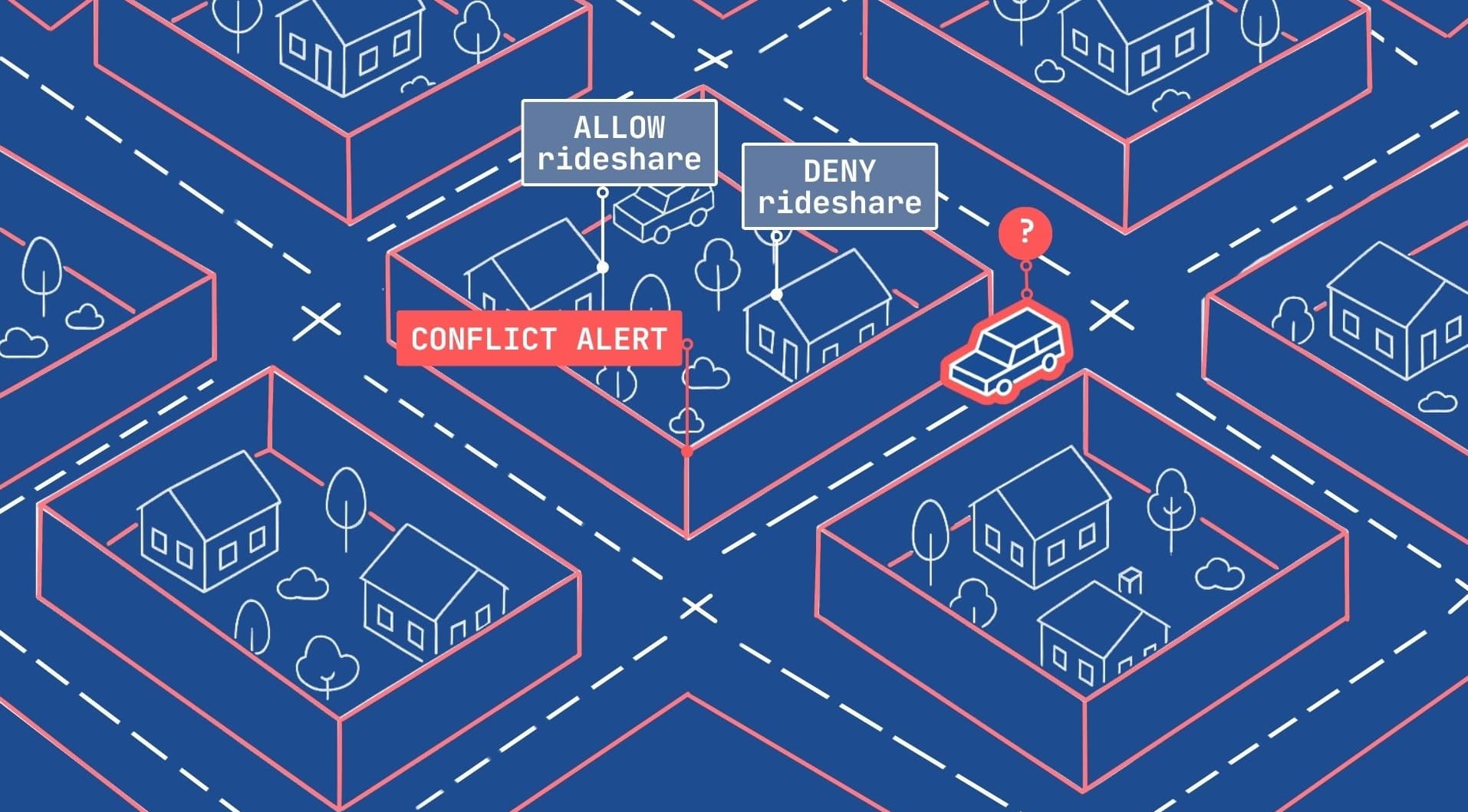
To say that microsegmentation is complex at scale is a bit of an understatement. In today’s world where we are constantly adding new IoT devices, AI agents, and AI models, microsegmentation architects must determine for every one of those new elements which segment they live on, who can access them from different segments, and then set up all those crossfunctional rules.
As an analogy, imagine that your city wanted to offer more protection to citizens, so they built walls around each neighborhood and people would need to be authorized to cross those boundaries. So if you and your friends want to take a hike in a different neighborhood, you would each need authorization to cross those boundaries. Now imagine there is a new AI service that multiple people want to access, for this analogy we will call this a new rideshare business. The business must be authorized in every neighborhood individually. You can see how this would be extremely difficult to maintain over time.
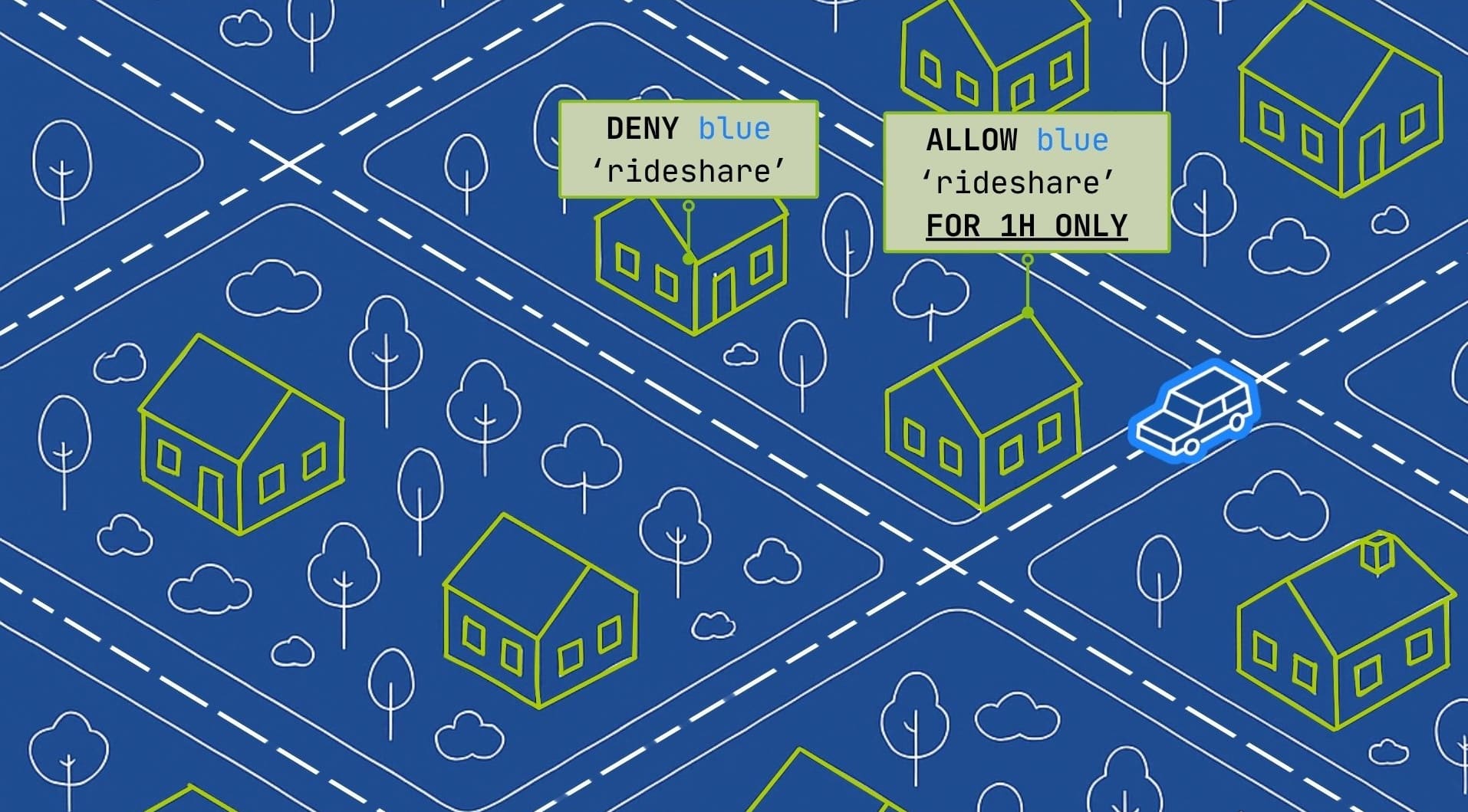
Introducing Picosegmentation
Moving on with our analogy, imagine that, instead of putting walls between neighborhoods, each person was protected individually. You could have a policy manager in the city who decided what services would be accessible, but the control could be at the individual level. This is what the atPlatform provides for security. Each element including services, servers, cloud instances, AI agents, AI models, IoT devices, or humans can be individually protected. In our analogy, each person would decide who had access to them.
This vastly simplifies network management while increasing security. If a bad actor gets into one device, they can only get into that device, they can’t make a lateral movement to other devices or services. This not only makes everything on the network safer, but it discourages attacks because the payoff is so low.
This architecture of picosegmentation is Zero Trust by design. Nothing trusts anything on the network by default. The atPlatform is an implementation of picosegmentation that cryptographically authenticates who you are at every interaction. Additionally, the atPlaform switches the current model of “connect then authenticate” to “authenticate then connect,” further limiting the potential attack surface.
Network Segmentation vs. Microsegmentation vs. Picosegmentation
Here is an overview of the differences between network segmentation, microsegmentation, and picosegmentation:
Implementation
The nice thing about network segmentation is that you can implement it over time, segmenting new networks as they come online. But with microsegmentation, you must decide on how zones are going to be set up and basically switch to microsegmentation as a whole. The implementation of microsegmentation is a much larger project, time intensive, and expensive.
However, picosegmentation is far simpler to implement. You can start with something simple like NoPorts and implement it first for your most critical resources – something like remote access for admins to important servers. As new services come online, such as AI agents or IoT resources, you can implement picosegmentation for anything new, then go back over time to bolster your entire network security profile over time with picosegmentation.
Microsegmentation in Practice
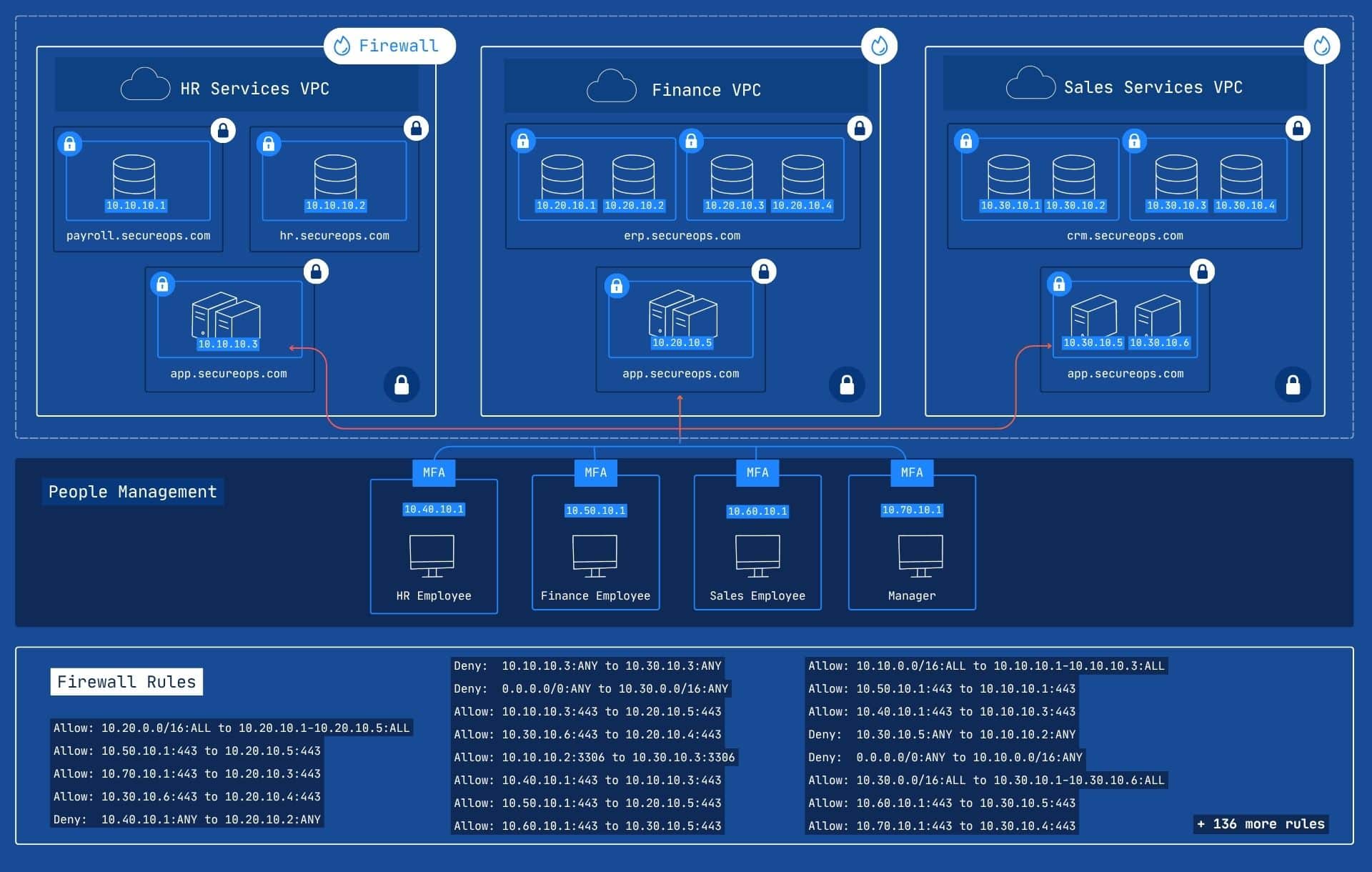
Picosegmentation in Practice
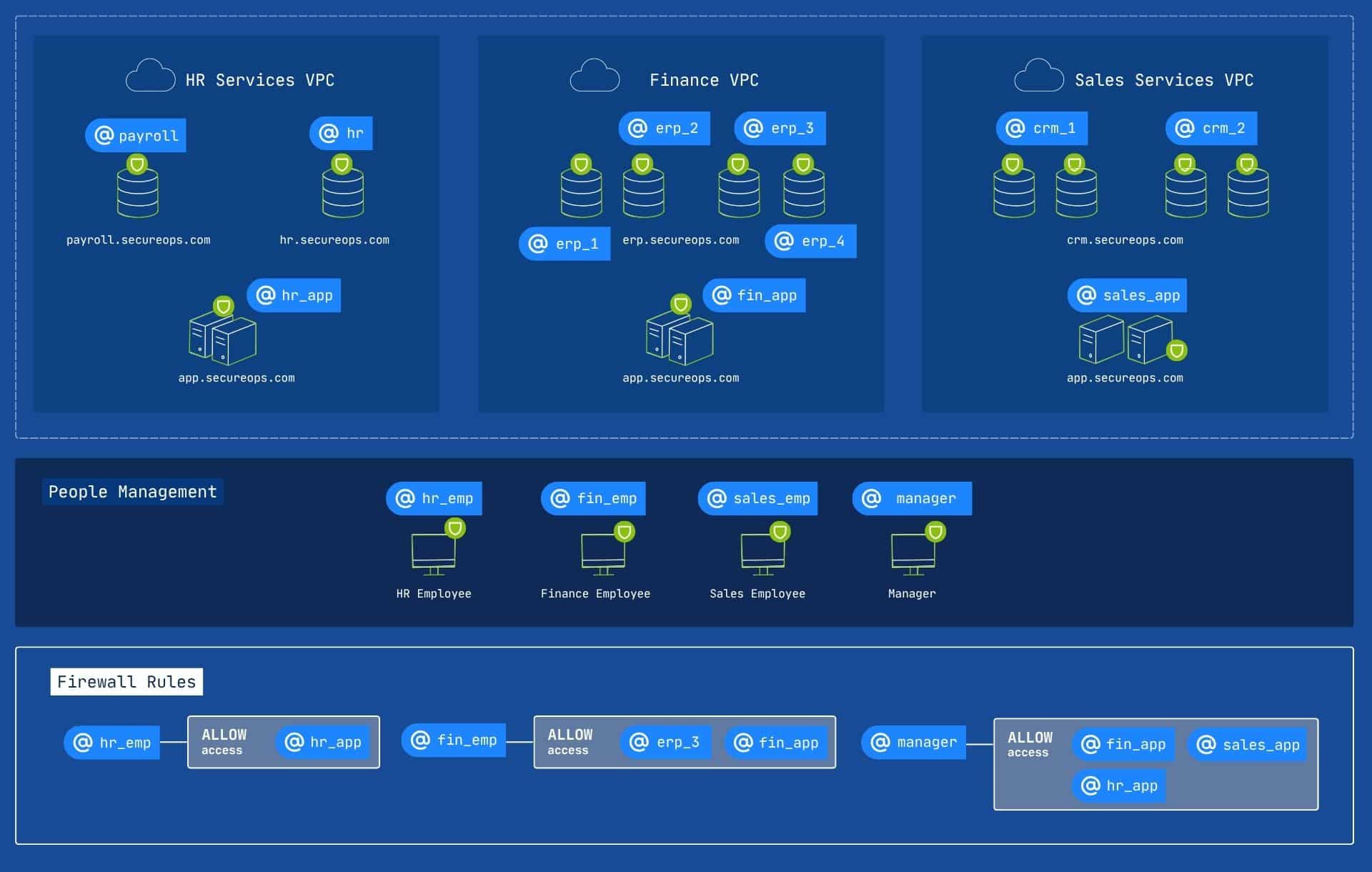
Diagram 4: With picosegmentation, the focus shifts to protecting individual elements within and across all VPCs. For HR, Finance, and CRM services, each interaction between any two elements (e.g., a user accessing a specific HR application, or a finance service interacting with a CRM module) is individually authenticated and authorized. This eliminates the need for complex firewall rules between VPCs, as security is enforced at the point of every connection, dramatically simplifying management while vastly enhancing overall security and limiting lateral movement.
Try out picosegmentation today with a free trial of professional NoPorts. A separate free version is available for personal use.
Where CEO Vision Meets CISO Approval: Launching AI Architect
AI Architect solves the enterprise AI bottleneck by combining visual architectural blueprints with a Zero Exposure foundation, allowing leaders to deploy secure, production-ready AI agents at 100x the speed of traditional coding.
The SDLC is Broken: Building Architectural Trust for Agentic AI
The SDLC is broken. As AI moves from chatbots to autonomous agents, here is how the architecture of trust must change.
The MCP Security Paradox: Why the “USB-C for AI” Is an Architectural Minefield
Model Context Protocol promises universal connectivity for AI, but its current architecture is scaling a broken trust model that leaves sensitive enterprise data vulnerable to exploitation.
How to Let AI Agents Act on Your Behalf Without Losing Control
Imagine your AI agent rebooking a canceled flight and hotel while you sleep—securely. Learn how the atPlatform solves the trust and permission problems of AI, allowing agents to act for you while you maintain total control.
Why 95% of GenAI Pilots Fail (and How to Ensure Yours Doesn’t)
Why do 95% of GenAI pilots fail? It’s not the AI—it’s the legacy infrastructure. Learn how to bridge the friction gap using Restricted Access Agents (RAA) to build a production-ready, secure future for your AI initiatives.