ARTICLE
The AI Chain of Trust: Secured by Atsign
Your AI Supply Chain Is a Ticking Liability
The integrity of your AI results is a direct reflection of the system that produces them. If the identities, data, and policies fueling the engine aren’t secure, the decisions coming out of it can’t be trusted. And that risk is magnified when you’re collaborating across different organizations. In a traditional client-server model, the AI supply chain has inherent security risks. This architecture, with its centralized data and exposed network, creates a massive attack surface. It leaves the door wide open for data poisoning, model theft, and policy violations that result in audit failures, fines, and financial loss.
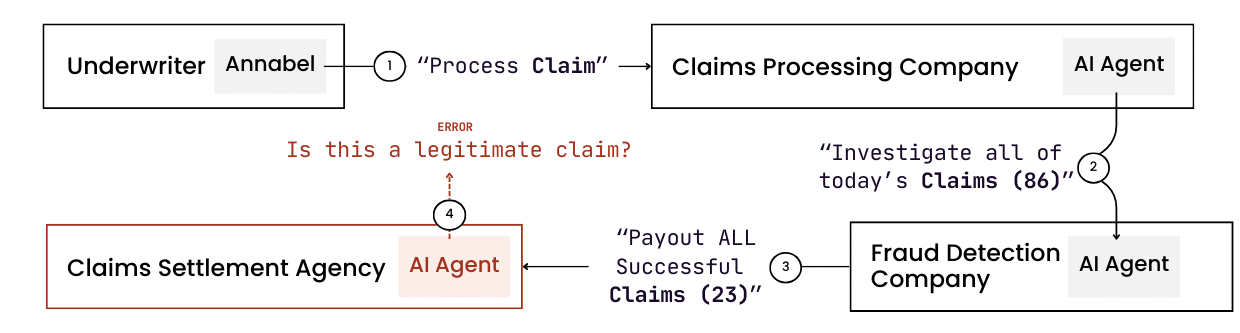
This is a problem of trust that becomes unmanageable when transactions span multiple companies. Consider this insurance claim scenario:
A human underwriter named Annabel at Global Insurers, Inc., instructs a Claims Processing AI agent, ‘ai-claims’ (hosted at a partner firm), to process a claim. That agent then coordinates with ‘ai-fraud’ at a third-party service and ‘ai-pay’ at a settlement agency. The critical question arises: How can “ai-pay” verify that this request truly originated from Annabel, an authorized human at a completely different company, without a direct line of sight?
Without a secure, machine-friendly way to verify this chain of trust, a single point of failure can lead to streams of fruadulent payouts, a critical audit failure, and millions in reputational damage.
How Atsign Creates a Foundation for the AI Chain of Trust
Atsign’s atPlatform is a patented approach to secure connections and data exchange. Using standard networking (TCP/IP) infrastructure, it re-architects how LLMs, AI agents, data, and people connect by moving security and control to the edge.
This allows you to build a verifiable, end-to-end chain of trust directly into the fabric of your AI operations. Here’s how:
Identity
The Core of Zero Trust
With the atPlatform, every person, entity, and AI agent is assigned a unique, cryptographically verifiable identity called an atSign. This is more than a user name; it’s a secure, portable address that cannot be impersonated. Every connection is authenticated using cryptographic keys, not passwords, so you know exactly who or what you’re communicating with, no matter where they are. This decentralized control gives each atSign absolute authority over its own identity and data, a critical capability when managing autonomous agents.
Policy
Dynamic and Granular Access Control
The atPlatform allows you to define simple, yet powerful, policy rules to grant or revoke permissions. These policies are enforced at the identity layer, not the network layer, providing unprecedented control over your AI systems. You can define fine-grained permissions for who can read, write, or share data with a specific AI model or agent. Crucially, these dynamic rules can be assigned for a single session or a specific time period, enforcing the principle of least privilege.
Signing & Encryption
Unbreachable Data Integrity
Our architecture ensures that data is encrypted at the edge, with cryptographic keys generated and stored on the device itself. This provides true end-to-end encryption from origin to destination, leaving no room for man-in-the-middle attacks. Every piece of data can also be digitally signed, creating a verifiable record of its origin and guaranteeing that it hasn’t been altered in transit or at rest.
Transport & Storage
The Invisible Network
By design, our core architecture removes the need for open listening ports on devices and servers. All connections are initiated outbound-only, making your AI agents and their data stores effectively invisible to external port scanners. This eliminates the attack surface created by open ports, ensuring that your AI infrastructure is secure by default.
The Verifiable AI Supply Chain
By leveraging a secure, peer-to-peer data exchange and a verifiable identity framework, the atPlatform enables AI provenance. This creates a clear history of every person, agent, database or LLM involved in every transaction.
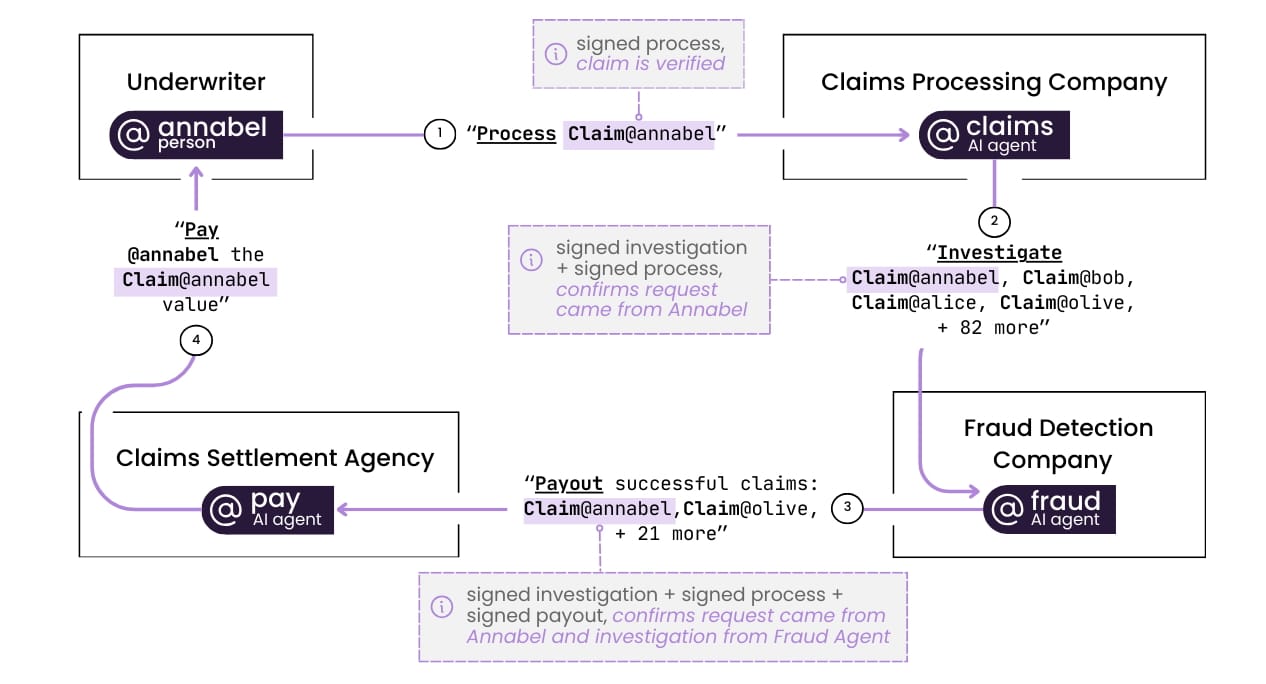
Let’s revisit the insurance scenario using the atPlaform. Now, each request is signed as the claim moves through the AI pipeline. This gives the payment AI, ‘ai-pay,’ a chain of cryptographic signatures proving that the request did, in fact, originate from the authorized underwriter, Annabel.
This allows the system to adhere to policy, verify authority, and provide a complete audit trail across all organizations involved in the claim.
Next Steps
Schedule a demo today to see how we can secure your AI infrastructure.
Understanding Picosegmentation for Network Security
Picosegmentation protects individual elements, simplifies management, and defends against lateral movement. It is a secure and easy to maintain alternative to microsegmentation.
Quick, Easy, & Secure GPU Arbitrage with Atsign’s atPlatform
Learn how atPlatform enables secure GPU arbitrage while cutting costs, minimizing downtime, and simplifying workload migration.
New Legislation Poised to Give People More Control Over Their Data
Utah has passed the Digital Choice Act, landmark legislation that could reshape how social media applications handle people’s data.
Shifting the Paradigm: Atsign’s Organic Security Approach
Atsign’s built-in security—encryption, zero trust architecture, and a least privilege approach—performs better than firewalls and authentication systems.
The One Question Boards Should Be Asking Their Companies: “How Are You Securing Your AI?”
Boards must prioritize AI security. Learn what questions to ask companies about AI security strategy, including data protection, access control, and vulnerability management.