ARTICLE
Your Digital Doors Are Wide Open: An Urgent Warning
The FBI has a clear message for every organization: close your open network ports. This isn’t just a technical recommendation; it’s a critical warning about gaping holes in your digital defenses that cybercriminals are actively exploiting. While many are embracing modern “Zero Trust” security, far too many businesses are still leaving their digital doors not just ajar, but wide open.
Understanding Your Digital Doors
Imagine your company’s online presence as a building. For information to flow in and out – like emails, website visits, or remote work connections – you need various entry points. In the world of computers and networks, these are called ports.Think of ports like numbered doors on your building:
- Ports 80 and 443 are like the main entrances for your public website.
- Port 22 might be a side door for IT staff to manage servers remotely.
- Port 3389 could be a dedicated line for remote access to a computer.
When a port is “open,” that door is unlocked and accessible from the internet. When it’s “closed,” that door is not only locked but also invisible to anyone looking at your building from the outside.
The Illusion of Necessity
Why would any business leave these doors open? Historically, some systems needed open ports to function. Your public website, for example, needs an open port to let customers in. But most open ports aren’t for your public website. They’re often left open for:
- Remote access for employees or partners.
- Legacy systems that weren’t built with security in mind.
- Connections to partners or cloud services that were set up without enough thought for security.
- Simple oversight – IT teams are busy, and sometimes these doors are just forgotten.
The Alarming Reality: How Easy It Is to Find Your Open Doors
Cybercriminals don’t need to be master hackers to find your open ports. They use simple, automated tools that constantly scan the internet. Imagine someone walking down your street, rattling every doorknob. Tools like Nmap can quickly scan an entire company’s network, revealing every single open port like a flashing sign.
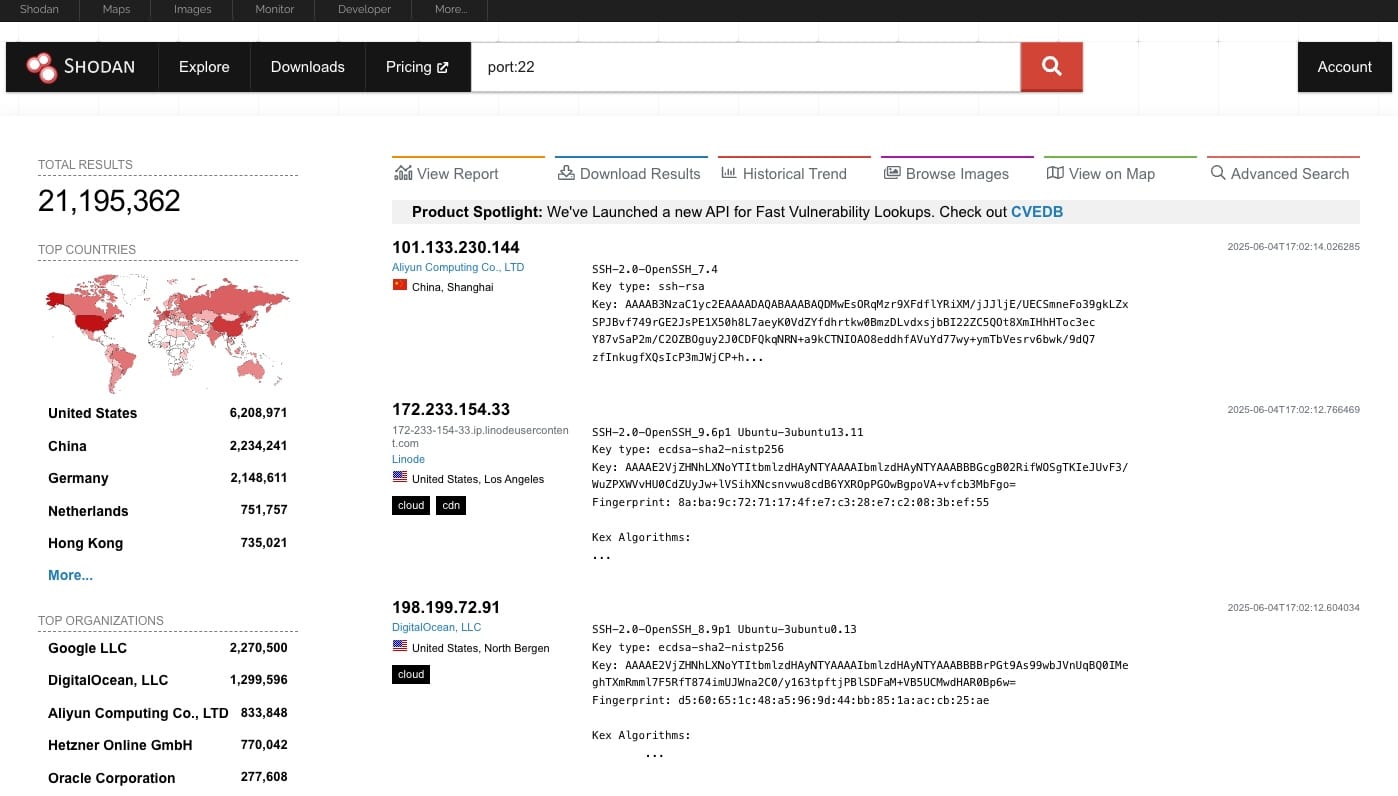
It gets even easier. There are public search engines, like Shodan.io, that constantly scan the internet for open ports on all connected devices. Imagine Google, but instead of finding websites, it finds servers, cameras, and everything else online.
For example, if you search Shodan.io for “port:22” (a common port for remote access), you’d instantly see over 21 million of devices worldwide with that port open. This shows how incredibly simple it is for anyone – including cybercriminals – to find potential weak points.
The Consolidating Threat: You’re Becoming a Prime Target
Here’s the urgent truth: The cybersecurity world is changing fast. More and more organizations are aggressively closing unnecessary open ports.
This means the hunting ground for cybercriminals is shrinking. If most companies fortify their digital buildings with strong locks, who do you think the burglars will focus on? The few remaining with unlocked doors.
If your organization still has unnecessary open ports, you’re painting a bullseye on your back. You’re making yourself the easiest target in a world where everyone else is boosting their defenses.
Beyond Public Websites: The Path to Better Security
The good news is that most operations no longer need constantly open ports. While public websites need them, almost everything else can, and should, operate with closed ports.
Today’s “secure access” solutions try to help, but they aren’t perfect:
- VPNs (Virtual Private Networks) – These create a secure tunnel, but the VPN server itself still has one open door. If that single, critical door is breached, attackers can often roam freely inside your network. VPNs also demand significant setup, ongoing maintenance, and can be costly to expand.
- “Zero Trust” Solutions – These aim to verify every user and device before granting access. While better, they often rely on a middleman service that still has its own open doors to manage connections. If that middleman is compromised, it could expose many customers. These solutions can also be complex to set up and come with high subscription fees.
- API Gateways – Used for system-to-system communication, these act like a receptionist for your backend systems, handling requests through one or two controlled doors. But like any software, they can have hidden flaws (zero-day vulnerabilities) that allow attackers to sneak past. They also add complexity and cost to your IT setup.
- Secure Tunnels – These create encrypted connections between systems. While they often start from inside your network, the endpoint still needs a specific, discoverable port. Managing these across complex networks can be a nightmare and introduce new risks if not done perfectly.
The bottom line: These solutions are steps in the right direction, reducing your risk. But they don’t eliminate it. They introduce new layers of complexity, cost, and in some cases, new trusted third parties, leaving you still vulnerable to sophisticated attacks.
The Business Value of True Port Elimination: Why Your Future Depends On It
Securing your digital entry points isn’t just an IT task; it’s a vital business decision with real financial and reputational impacts:
- Avoid Catastrophic Costs – A single cyberattack, often starting with an open port, can cost millions in ransom, recovery, and lost business.
- Protect Your Brand – A data breach destroys trust and damages your reputation, leading to lost customers and revenue.
- Lower Insurance Bills – Insurers are watching. Strong security, especially eliminating open ports, can lead to lower cyber insurance premiums.
- Ensure Business Keeps Running – An attack can shut down your operations for days or weeks, leading to massive losses in productivity and missed deadlines.
Building a Truly NoPorts Future
Current “secure access” solutions are improvements, but they still leave a detectable entry point somewhere. This means organizations are constantly playing defense, managing complex systems, and hoping no one finds a flaw in their layers of protection.
The industry is now moving towards a revolutionary new way: one where no inbound network ports are ever exposed to the public internet, period. Atsign’s atPlatform and NoPorts provides a world where:
- Your systems are invisible – There are no open ports on anything with anything that matters.
- Authentication happens first, always – No connection is ever allowed until both the user and their device are strongly verified, ensuring only trusted entities can even attempt to connect.
- Every communication is fully encrypted – All data is automatically protected, making it unreadable to anyone without permission.
- Your identity is the new security perimeter – Protection is built around who and what is trying to connect, not where they are or what doors they can see.
This isn’t just about reducing risk; it’s about fundamentally changing the rules of the game. By eliminating open ports entirely, you take away cybercriminals’ easiest ways in. You move beyond just controlling access to actively preventing discovery altogether.
The time to act is now. Don’t be the last organization with digital doors that can be found and exploited. With NoPorts, your digital assets are invisible and inaccessible until explicitly authorized. Safeguard your financial future, protect your brand, and ensure your business keeps running. Close your digital doors, and make them disappear.
Where CEO Vision Meets CISO Approval: Launching AI Architect
AI Architect solves the enterprise AI bottleneck by combining visual architectural blueprints with a Zero Exposure foundation, allowing leaders to deploy secure, production-ready AI agents at 100x the speed of traditional coding.
The SDLC is Broken: Building Architectural Trust for Agentic AI
The SDLC is broken. As AI moves from chatbots to autonomous agents, here is how the architecture of trust must change.
The MCP Security Paradox: Why the “USB-C for AI” Is an Architectural Minefield
Model Context Protocol promises universal connectivity for AI, but its current architecture is scaling a broken trust model that leaves sensitive enterprise data vulnerable to exploitation.
How to Let AI Agents Act on Your Behalf Without Losing Control
Imagine your AI agent rebooking a canceled flight and hotel while you sleep—securely. Learn how the atPlatform solves the trust and permission problems of AI, allowing agents to act for you while you maintain total control.
Why 95% of GenAI Pilots Fail (and How to Ensure Yours Doesn’t)
Why do 95% of GenAI pilots fail? It’s not the AI—it’s the legacy infrastructure. Learn how to bridge the friction gap using Restricted Access Agents (RAA) to build a production-ready, secure future for your AI initiatives.